Secure your Kubernetes environment
Deploy, monitor, and secure your Kubernetes environment efficiently and at scale. Get best practices to secure Kubernetes.

How well do you understand your Kubernetes environment’s security posture?
I need visibility into my Kubernetes environment, but my MDR doesn’t monitor it
I need to secure my Kubernetes environment without slowing down developers
I need to learn how to manage a new attack surface (without any staff)
I need to improve my Kubernetes security posture to prevent issues before they occur
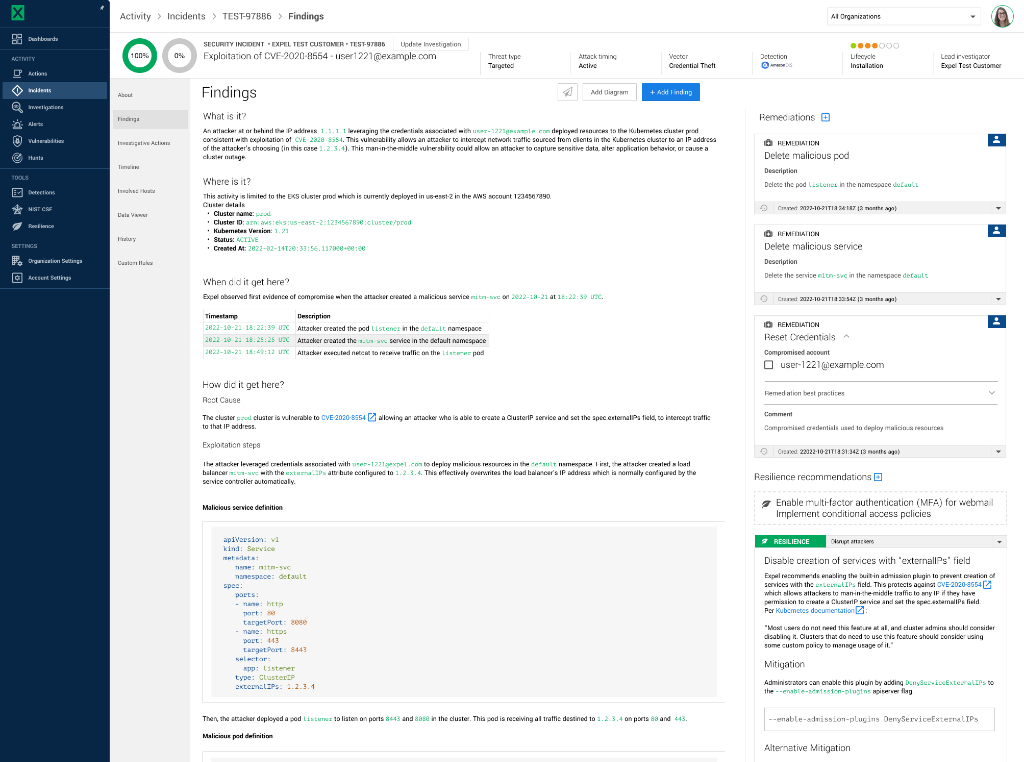
Expel MDR for Kubernetes
Eliminate blind spots, help DevOps maintain a secure infrastructure, and free up developers to focus on building business-critical applications with advanced Kubernetes (k8s) monitoring for your clusters.
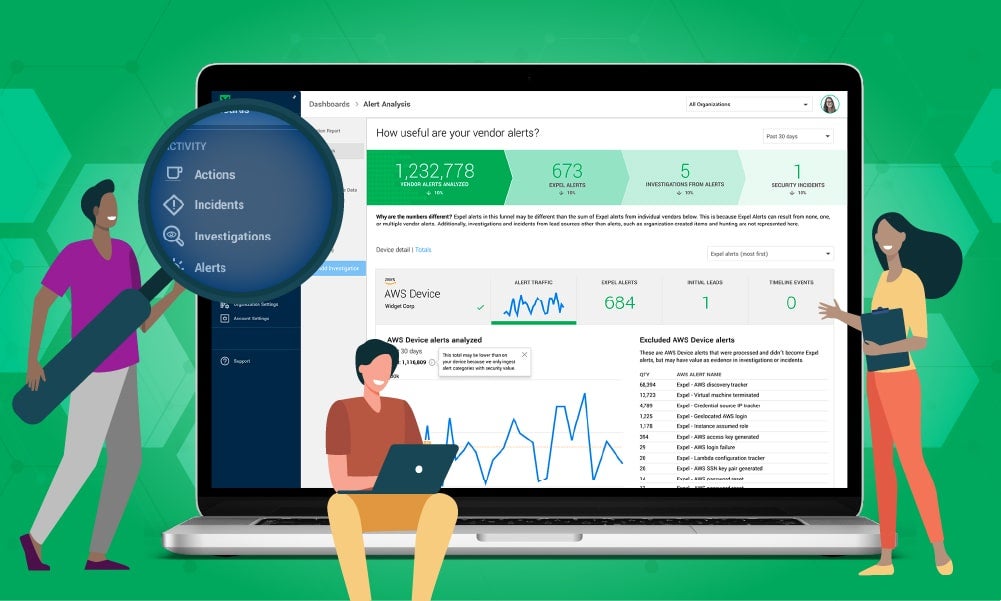
With the rapid adoption of container applications through Kubernetes, security operations teams need coverage across all attack surfaces. However, many businesses have a significant number of unmonitored applications within their Kubernetes clusters.
This is where Expel MDR for Kubernetes comes into play. It monitors your clusters, allowing you to adopt Kubernetes at scale without security concerns. Our platform generates usable insights, not just alerts, and it’s compatible with Amazon Elastic Kubernetes Service (EKS), Azure Kubernetes Service (AKS) and Google Kubernetes Engine (GKE).
Our (Expel-written) detections are designed to adapt and learn from your Kubernetes cluster’s activity, so you can stay ahead of potential threats. Kubernetes monitoring and detections align to the MITRE ATT&CK framework, allowing you to quickly remediate risks and build resilience for the future.